Update: Microsoft Deactivated Crypto-Jacking Mining Virus Embedded in Kobe Bryant’s Photo
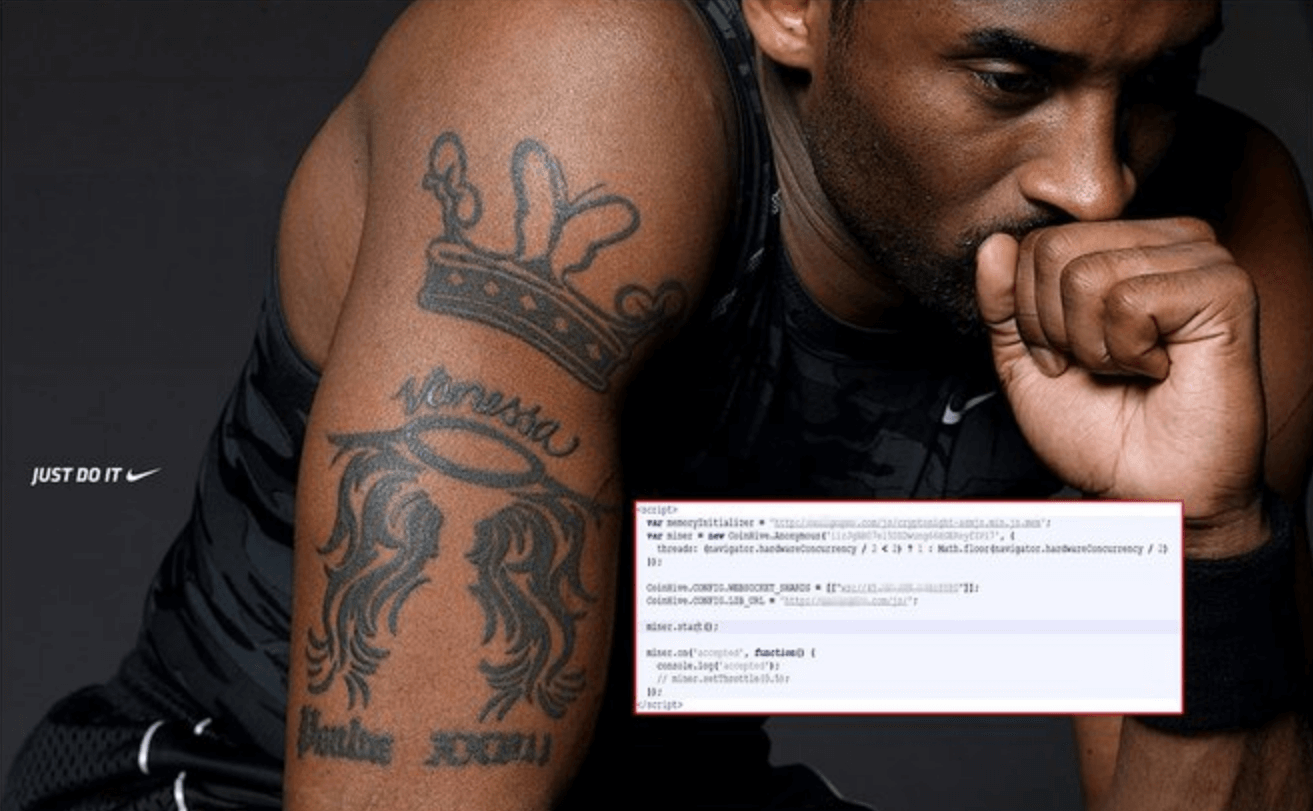
An elaborate scheme to illegally mine Monero hidden within Kobe Bryant image has been successfully blocked by Microsoft.
Kobe Bryant was a Legend
Earlier, there were reports that cybercriminals had devised an elaborate trick to illegally mine Monero, a cryptocurrency, by hiding a mining code inside Kobe’s photo.
Kobe died earlier this week in a tragic helicopter accident and was among the nine people who perished in the early morning crash.
Before his death, the basketball legend was highly regarded in the sporting circles and had initiated several community programs to empower local children and to promote the sport in the United States.
Given his popularity, his death came as a shocker and his family were condoled by global leaders including President Donald Trump, Barack Obama, influencers in the sporting community, and leading celebrities.
Microsoft Intervenes
With the attention, Windows noted that cybercriminals had hatched a plan and embed a mining code within Kobe’s image.
“While the world mourns the loss of an NBA legend, cybercriminals are, as expected, taking advantage of the tragedy. We found a malicious HTML file posing as a Kobe Bryant wallpaper that contains a coin mining script.”
Upon activation, the code will execute and begin using the individual’s computing power to illegally mine XMR, the native currency of the privacy-focused blockchain.
The practice is called steganography, and the process of illegally mining crypto currencies through a self-executing code is Crypto Jacking.
Criminals prefer to embed such codes in pictures of leading celebrities considering how viral they can become. The higher the chances of being shared widely, the more they are clickable and hence mine more coins before spreading to different systems.
To protect users, Microsoft updated the community saying they had blocked the hosting website:
“Microsoft Defender SmartScreen blocks the website hosting the coin miner. Microsoft Defender ATP detects the malicious HTML file as Trojan.”
Other Cases of Crypto-Jacking
In August 2019, the French cyber unit wing, cyber gendarmes, deactivated a crypto-jacking bot, that had allegedly infected over 850k servers.
Its head, as BBC reported, was in France and was first identified by Avast, an anti-virus firm.
Jean-Dominique Nollet, the head of the Center for Combating Digital Crime (C3N), said:
“Basically, we managed to detect where was the command server, the control tower of the network of infected computers, the “botnet.” It was copied, replicated with a server of ours, and made to do things that allow the virus to be idle on the victims’ computers.”
Recent Posts
- Crypto News
Breaking: Bitwise Files S-1 For SUI ETF With U.S. SEC
Crypto ETF issuer Bitwise is looking to add a SUI ETF to its growing list…
- Crypto News
Crypto Hacks 2025: North Korean Hackers Steal over $2B in ETH and SOL This Year
In 2025, crypto hacks increased significantly. The cybercriminals associated with the North Korean government stole…
- Crypto News
Universal Exchange Bitget Removes Barriers to Traditional Markets, Offers Forex and Gold Trading to Crypto Users
The number one universal exchange Bitget is removing barriers between crypto and traditional finance. It…
- Crypto News
Breaking: U.S. CPI Inflation Falls To 2.7% YoY, Bitcoin Price Climbs
The U.S. CPI inflation came in well below expectations, providing a bullish outlook for Bitcoin…
- Crypto News
Crypto Market Brace for Volatility Ahead of Today’s U.S. CPI Data Release – What to Expect
The crypto market could see some price fluctuations ahead of the release of the major…
- Crypto News
Breaking: Canary Capital Files S-1 for its Staked INJ ETF
Canary Capital amended its staked INJ ETF application with the U.S. Securities and Exchange Commission…