Nearly $50M in USDT Stolen After Address Poisoning Scam Targets Crypto Trader Wallet

Highlights
- Address poisoning scam redirected $49.9M USDT after a routine test transfer.
- Spoofed wallet entries in transaction history triggered the mistaken transfer.
- Stolen funds were swapped to DAI, converted to ETH, then sent to Tornado Cash
A cryptocurrency trader has lost nearly $50 million in USDT after falling victim to an address poisoning scam, a technique that exploits transaction history rather than smart contract flaws. Blockchain security firms said the incident highlights how routine wallet habits can expose users to large-scale losses.
In an X post, on-chain analytics firm Lookonchain reported that the victim transferred 49,999,950 USDT to an attacker-controlled wallet on Dec. 20. The funds had just been withdrawn from Binance and were intended for the trader’s own address. Instead, they were redirected to a visually similar address created by the attacker.
Address Poisoning Scam Exploits Spoofed Addresses
The incident began with a test transaction. The trader sent a 50 USDT test transaction to confirm the destination address. Shortly after, an automated script generated a spoofed wallet designed to resemble the legitimate address.This step marked the start of the address poisoning scam.
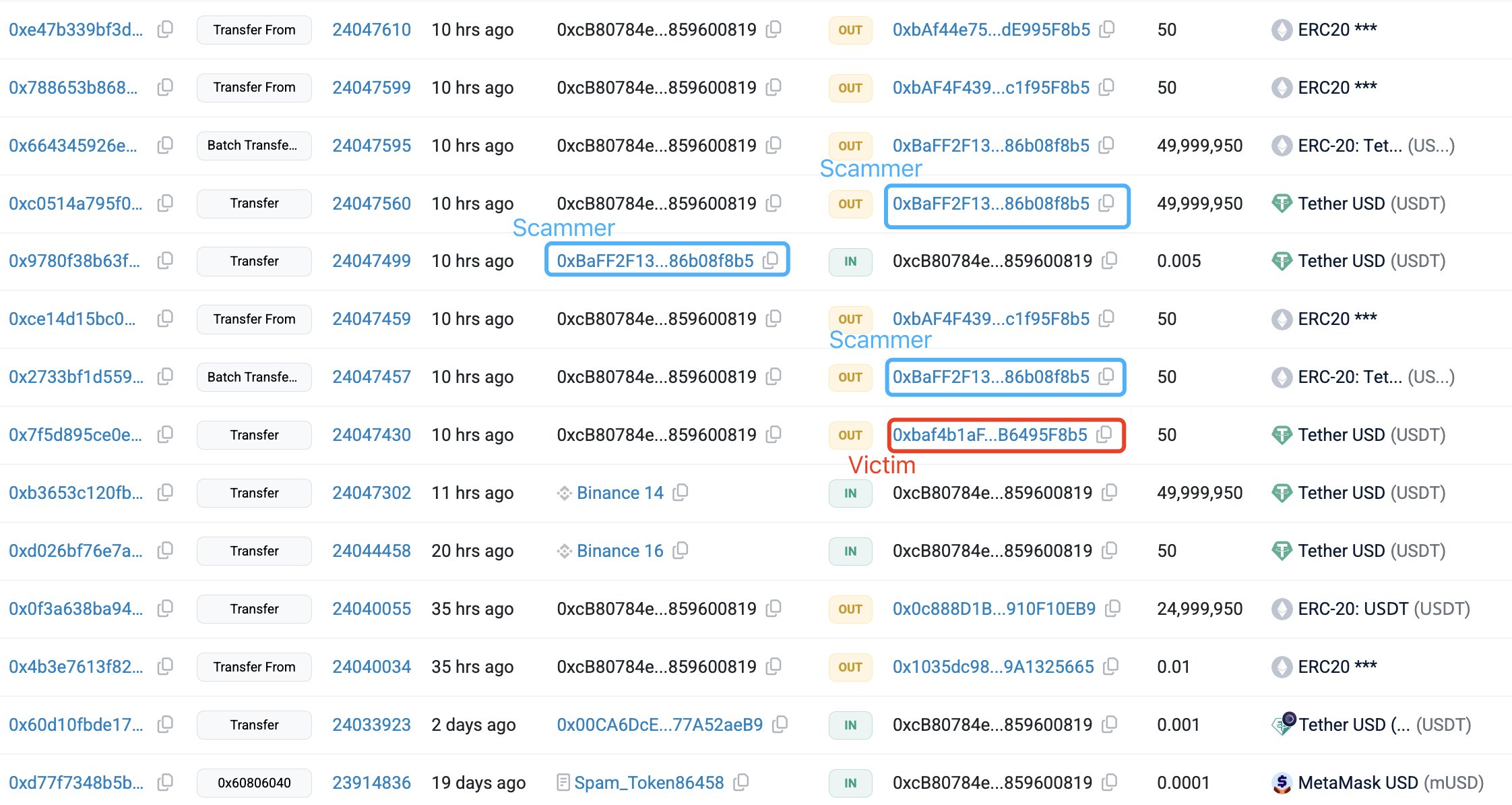
The fraudulent address shared the same opening and closing characters as the intended wallet, with differences confined to the center of the string. Many wallet interfaces shorten these middle characters, reducing visibility during routine checks.
By exploiting this display behavior, the attacker sent small transactions from the lookalike address to the victim’s wallet. This inserted the fake address into the transaction history, causing it to appear legitimate during later transfers.
When the trader later copied an address from their history to complete the full transfer, the lookalike address was likely selected by mistake. Etherscan data shows the test payment was sent at 3:06 UTC. The erroneous $50 million transaction followed roughly 26 minutes later, at 3:32 UTC.
Stolen Funds Moved Through DAI, ETH, and Tornado Cash
Blockchain security company SlowMist reported that the attacker moved quickly in order to minimize recovery risk. In 30 minutes, the $50 USDT was exchanged for DAI by via MetaMask Swap. The decision was strategic because Tether can freeze USDT if it’s associated with illicit activity, but DAI doesn’t come with any centralized freezes.
The DAI was then converted by the attacker to approximately 16,690 ETH. Approximately 16,680 ETH was deposited into Tornado Cash. The mixer was an attempt to obfuscate the transaction trails, the usual step subsequent to an address poisoning scam.
Upon executing the transaction, the victim sent an on-chain message to the attacker by a $1 million white-hat bounty. The offer demanded the repayment of 98% of the stolen money. There has been no public acknowledgement or reply. The security companies remain active monitoring the address poisoning scam.
According to Chainalysis, the incident contributes to a year of rising crypto thefts. Losses in crypo hacks 2025 exceeded $3.4 billion, more than the previous year. One of those, a February breach of Bybit by North Korea-linked actors, totaled about $1.4 billion and was the largest crypto theft ever.
- CLARITY Act: Trump’s Crypto Adviser Says Stablecoin Yield Deal Is “Close” as March 1 Deadline Looms
- Trump Tariffs: U.S. To Impose 10% Global Tariff Following Supreme Court Ruling
- CryptoQuant Flags $54K Bitcoin Risk As Trump Considers Limited Strike On Iran
- Why Is Bitdeer Stock Price Dropping Today?
- Breaking: U.S. Supreme Court Strikes Down Trump Tariffs, BTC Price Rises
- Ethereum Price Rises After SCOTUS Ruling: Here’s Why a Drop to $1,500 is Possible
- Will Pi Network Price See a Surge After the Mainnet Launch Anniversary?
- Bitcoin and XRP Price Prediction As White House Sets March 1st Deadline to Advance Clarity Act
- Top 3 Price Predictions Feb 2026 for Solana, Bitcoin, Pi Network as Odds of Trump Attacking Iran Rise
- Cardano Price Prediction Feb 2026 as Coinbase Accepts ADA as Loan Collateral
- Ripple Prediction: Will Arizona XRP Reserve Boost Price?
















